14 Emergent Technologies
This is a book about accessing, manipulating, analyzing, visualizing, and interpreting data, but urban informatics is more than just data and analysis. The definition I offered in Chapter 1 was “the use of data and technology to better understand and serve communities.” It is important not to lose sight of the word “technology” in that definition, as there are numerous technologies that have been incorporated into policy, practice, and services in recent years and promise to offer important advances. These include things like sensor networks, 5G cellular service, and blockchain. Of course, these technologies are not independent from data. In fact, they help us to generate, organize, and use data. Thus, a full understanding of the potential of urban informatics requires understanding the opportunities for these technologies. Introducing these technologies is the focus of this chapter.
14.1 Structure and Learning Objectives
This chapter will focus on three emergent technologies that have opened up new opportunities for policies, practices, services, and other products related to communities:
- Sensor networks that track environmental conditions across a city;
- 5G, the newest generation of the cellular network;
- Blockchain, which is an innovative way to create security in tracking the history of items.
The chapter will offer a conceptual overview on each of these three technologies with a five-part structure very similar to the previous chapter: (1) What it is; (2) How it works; (3) Ethical considerations; (4) Major applications; and (5) Additional reading. Note that this chapter does not have the “When to use it” sub-section. Whereas statistical tools have specific data structures and research questions for which they are best suited, the appropriateness of technologies is more easily summarized in terms of their applications. Again, these overviews will not make you an expert just yet but will provide enough base knowledge for you to discuss them, consider how they are relevant to your own community or work, and even to find additional resources by which you could learn how to use them yourself.
14.2 Sensor Networks
14.2.1 What It Is
Imagine opening a weather app in the morning to find out the current conditions, but instead of entering your town or city, you can enter your street block, or the address where you work. The web site would then tell you the temperature, humidity, precipitation, and air quality at that precise location, plus the current rate of pedestrian, car, and bike traffic. It might even forecast what these metrics will look like throughout the day. This is the vision for sensor networks in cities. With sensors placed on every street corner, we could be aware of conditions throughout the city with unprecedented precision at all times. This could be used by practitioners to deploy services, drivers to plan their commute, community organizations to prepare for storms, and so on. An example from Chicago called the Array of Things is depicted in Figure 14.1, including the design of a single sensor node and the placement of nodes around the city.
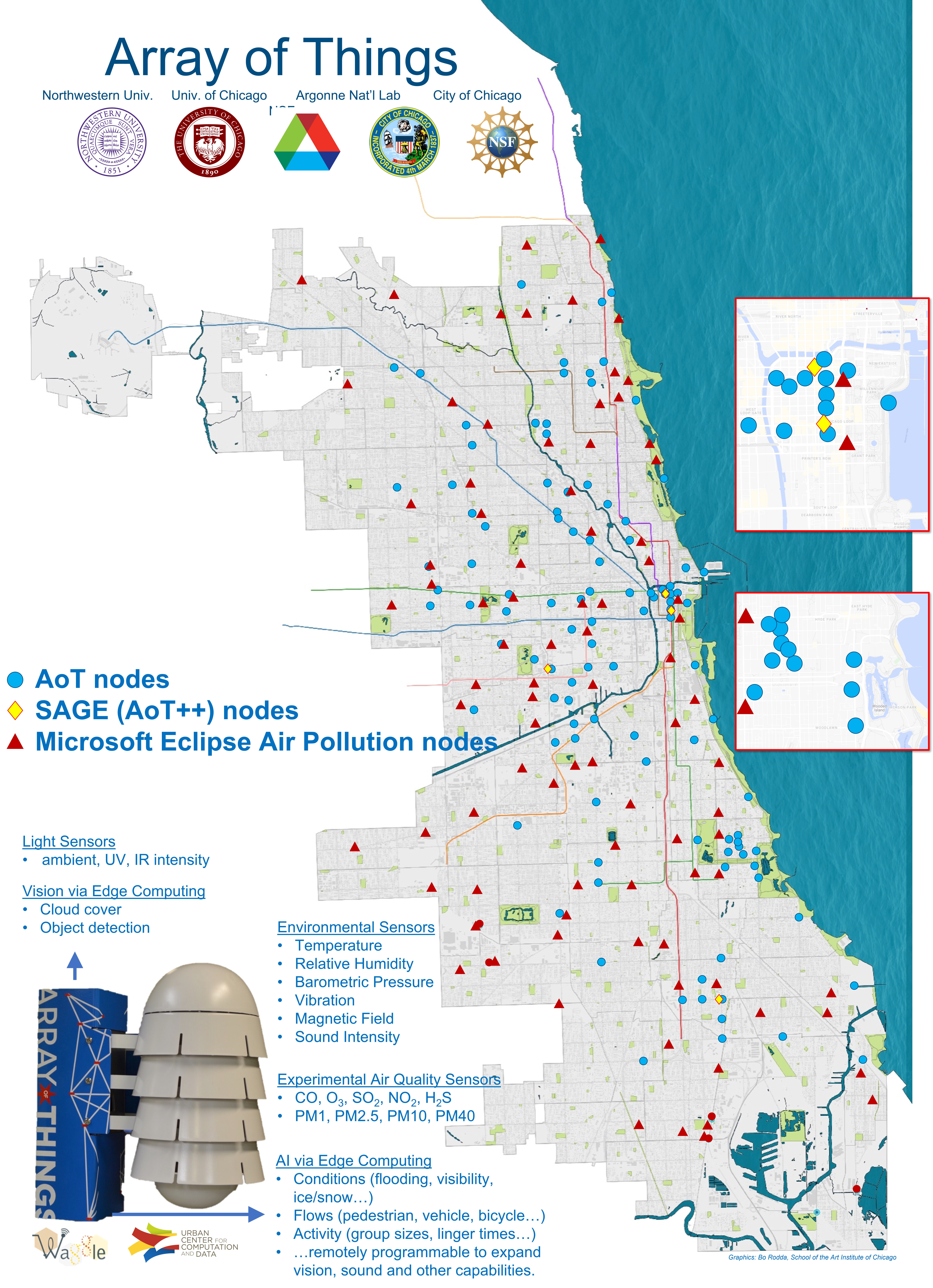
Figure 14.1: The Array of Things project has installed sensor “nodes” (see inset for what an individual node looks like) across Chicago, IL, to capture various conditions locally to gain a composite view of temperature, humidity, sound, light, and air quality, among other things, throughout the city. (Credit: http://arrayofthings.github.io)
14.2.2 How It Works
In some ways, sensor networks are deceptively simple. They consist of multiple individual sensor boxes, or nodes, each one containing at least one sensor. Each sensor collects a single type of information. There are sensors that measure light, sound, temperature, the rate of precipitation, one of numerous forms of air pollution, and more. There are sensors that note the presence of smart devices as people pass with phones in their pockets. Some sensor boxes include video cameras. Thus, a single sensor box might include any mixture of these. Typically, every node in a sensor network contains the same collection of sensors, though there might be reasons to have some nodes contain more or fewer sensors than others depending on their placement or cost considerations.
Sensors generate measures at a predetermined frequency (e.g., every minute, every hour, etc.). These measures are then combined by the node and transmitted by WiFi and cellular networks to a centralized server. The centralized server receives these from all nodes in the network and organizes them into a giant database that includes measures for all conditions, from all locations in the network, for all timepoints at which data were generated. As such, it is a uniquely detailed archive of conditions across space and time. The scope of these observations is determined by the number and diversity of nodes, the number of conditions measured, and the frequency of reporting.
The original measures often need to be processed in some way, which can happen before transmission to the server by computer chips inside the sensor box, or after transmission once the data are on the server. The nature of this processing varies by the measurement type. Pollution needs to be adjusted for wind speed, for example. Meanwhile, machine learning algorithms can be used to tag video content as containing people, cars, or bikes, thereby tracking different forms of traffic.
14.2.3 Ethical Considerations
The ethical considerations of sensor networks vary with their ambitions. Tracking temperature and air quality does not raise many eyebrows beyond the anticipation that the data will be used appropriately to maximize public welfare. Tracking radio frequency identifications (RFIDs) from smartphones or taking videos of pedestrians is much more sensitive and potentially alarming. Many communities have actively rejected efforts to put such technologies in public spaces owing to fears that they can violate privacy. A sensor network designed by the University of Chicago and the City of Chicago called Array of Things (the same one depicted in Figure 14.1) had to remove RFID trackers from their nodes because of public backlash. They did this even though the trackers in the proposed nodes had been designed to guarantee anonymity, highlighting just how uncomfortable such technologies can make people. The same project, though, offered a potential solution to the tradeoff between videos offering both uniquely valuable and uniquely invasive information. They developed algorithms for pre-processing video within the node to extract information like “number of cars” and “number of pedestrians.” The node then transmits these non-invasive metrics while deleting the original video footage.
In the end, the biggest question pertaining to sensor networks in public spaces is: What does the community want? This question has two sides to it. The first is comfort with the technology. If the community is comfortable with video cameras and RFIDs, then implementing them could be just fine. If the community is not, then that is not an option. The second is how the sensor network and the information it generates might benefit the community or address local challenges. Ideally, these solutions might be co-designed by community members, technical experts who would build them, and the agencies or corporations that would implement them. A difficulty around sensor network implementation is that they have been imagined and deployed by corporations in a top-down fashion. This process often fails to incorporate community voices to co-design the sensor networks to best reflect community interests and concerns.
14.2.4 Major Applications
Array of Things was billed as a “fitness tracker for the city” in Chicago. Efforts in other cities from private corporations have offered similar promises. And the promise is substantial. Again, imagine being able to know and forecast a broad range of conditions for every street block in the city in real time. The question, though, is whether the ambitions (and costs) of placing sensor nodes on every street block match the need and promised benefits. The answer to this is mixed and relies on specific use cases. For instance, recent work (by the Boston Area Research Initiative , in fact) found that summer temperature varies not just across neighborhoods but from street to street within neighborhoods, and that these localized differences drive disparities in medical emergencies during heat advisories (O’Brien et al. 2020). Preliminary analyses suggest that there are similar “microspatial inequities” in air pollution as well (Gately et al. 2017). These findings provide a justification for putting sensor nodes on every street, but to what end? We do not yet have programs or services that are able to capitalize on information that is this precise. More often policies are designed to be uniform across the city or, at most, neighborhood specific.
For the reasons described in this section and the previous (Section 14.2.3), sensor networks have yet to realize their potential. They have not been developed and designed with community needs in mind. They assume microspatial inequities but are needed to prove that those same inequities are present; otherwise the sensor networks are not needed. There is then the question of what types of action they could inform and instigate through the information they generate. But without evidence for the spatial and temporal variation in conditions that only sensor networks can track, no one has developed programs and services that are responsive to them. This is not to say that solving these issues is impossible, but it does capture how sensor networks, once seen as the infrastructure of the future, are trapped in a chicken-or-egg dilemma. Do we need sensor networks to address issues that only they can observe to enable activities that we have not developed because we do not know if we need them? The jury remains out.
14.3 5G Cellular Networks
14.3.1 What It Is
5G is the newest generation of the cellular network. At the time of this writing, most of the world is still operating at 3G, 4G, or earlier cellular systems. 5G is estimated to be 100 times faster than 4G, to have the capacity to accommodate thousands more devices over the same geographic scale, and to have 1/200th the latency (that is, the time it takes the network to respond to a request). These three metrics, apart from sounding like a sales pitch, reflect rather remarkable advances to the three parts of a cellphone network’s function that matter: speed, capacity, and latency.
14.3.2 How It Works
Cellular networks work on radio waves, which can have low, medium, and high frequency. Low frequency is the traditional tool for covering large areas and have been the basis of TV, radio, and all generations of cellphone network through 3G. Medium frequencies are specifically used in WiFi. They were incorporated into 4G and have proven very useful in adding capacity locally. High frequency radio waves are used especially for sensors and satellites. 5G is the first generation of the cellular network that uses high frequency radio waves.
Using high frequency radio waves has multiple advantages. The simplest is that high frequency waves can support higher speeds. They also target each device with a greater precision that is not available from medium or low frequency waves. This allows 5G to support more devices more efficiently, reaching as many as 1,000,000 devices per square kilometer. Further, this precision and its efficiency will work better for devices that have small batteries, like smart watches or glasses, as the energy required to stay connected to the network is drastically lower. Last, high frequency waves provide a quicker back-and-forth between devices and the network, which reduces latency.
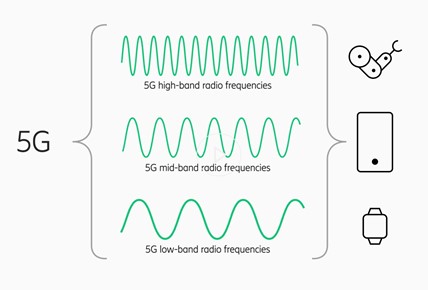
Figure 14.2: 5G cellular networks incorporate low-, medium-, and high-band radio frequencies in order to enhance speed and capacity and lower latency. This will enable to greater usage of “smart” technologies that require efficient, rapid connections. (Credit: Ericsson).
14.3.3 Ethical Considerations
5G technology itself does not raise a lot of ethical considerations. It simply improves speed, capacity, and latency in the cellular network. There are, of course, potential concerns over the technologies that it facilitates, like augmented reality, but those should be applied to critiques of those specific technologies rather than 5G. That said, the rollout of 5G should be watched closely. Right now, 5G is only available on a small proportion of the worldwide cellular network. As that changes, though, it is always possible (and even likely) that it will be available in more affluent communities in cities long before it reaches other places. This exacerbates digital divides between rich and poor and urban and rural. This is something for which we will need to be vigilant if the advances of 5G prove to be sufficiently important to give communities with access to it an unfair advantage relative to those without such access.
14.3.4 Major Applications
Some of the benefits of 5G are incremental. Greater speed for our devices is always welcome. Who would say no to being able to download a whole HD movie in a matter of minutes? Capacity is nice, too, though not necessarily game-changing. Cellphone companies advertise how everyone in a stadium can engage with the cellphone network simultaneously. That sounds nice but does not transform society. (A better case might be made around cellular networks not bogging down when everyone is trying to call others during an emergency.)
There are some more transformative opportunities, though, created by 5G. The lower latency is critically important for unlocking the power of AI-based devices that communicate with each other or otherwise respond to information received through the network. For example, one of the important parts of a transportation system based on autonomous vehicles is the ability for them to communicate with each other. Whereas humans use blinkers to indicate that they will turn or shift lanes, errors can be made that lead to collisions. In contrast, cars would tell each other when they were going to turn, change lanes, or otherwise shift their trajectory with perfect fidelity, leading to smooth coordination and the virtual elimination of crashes. These split-second communications and responses, however, require the low latency of 5G. Similarly, robots and other AI-based technologies also require low latency to gather, respond to, and transmit information, especially when they are intended to communicate with each other.
Additionally, the efficiency of connection with 5G expands opportunities for devices with small batteries. Innovations like smart glasses currently have power limitations, as they cannot accommodate batteries large enough to last more than a short period of time. But if they were able to connect to the network for a fraction of the energy expenditure, a battery could last a full day or even longer. This lays the groundwork for these and other small smart devices to proliferate in number and type.
14.4 Blockchain
14.4.1 What It Is
Bitcoin and other forms of cryptocurrency are a remarkable feat in that they have established markets and the basis for property in a completely virtual space. How is this possible in a world with increasing concerns around cybersecurity and reports of ransomware attacks? Is the system vulnerable to toppling with the clever invasion of a single hacker? The answer is a new technology called blockchain. Blockchain is a way of storing data in a secure way that is protected from manipulation by a single bad actor without being reliant on a single governing body or third party.
14.4.2 How It Works
Blockchain is a distributed database shared among the nodes of a computer network. We are going to break down what this means, but first it is useful to understand that it operates at two levels, each of which contributes to its unique system of security. The first is at the database level, the second is through the network that manages this database. How a blockchain works is also depicted in Figure 14.3, specifically for cryptocurrency.
The structure of a blockchain database is designed to ensure historical consistency, which is important for security in a variety of applications. Data in a blockchain are organized in “blocks” of a pre-determined size. Once a block is filled, it is closed and linked to previous blocks (hence, the chain). This creates an irreversible timeline that can be read but not be edited. Also, to alter one block in the chain would require changing all subsequent blocks to be consistent with the earlier change, which would be computationally difficult if not impossible given the way blocks are encoded based on each other. In these ways, the blockchain is protected against alteration.
Suppose a bad actor succeeds in breaking the read-only aspect of the blockchain database structure. This would undermine the promised security. The distribution of the database across multiple computers in a network offers a second level of security that guards against this. Every computer on the network has its own independent copy of the historical record of the blockchain. These copies are supposed to be identical, and the computers periodically confirm this with each other. If any computer disagrees with the others on the historical record—say, because someone attempting to modify the record for their own personal gain—the consensus overrides it and all copies revert to the agreed upon record. Someone looking to defeat this safeguard and alter the historical record would have to control more than 50% of the computers on the network. In a large network, like a cryptocurrency, this is practically impossible.
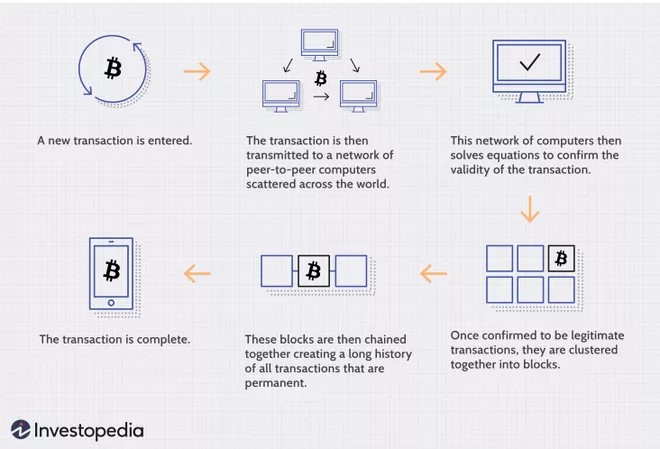
Figure 14.3: A depiction of how blockchain operates as a database of transactions, consisting of blocks, distributed across many computers (or nodes) on a network. (Credit: Investopedia)
14.4.3 Ethical Considerations
Much like 5G, there are not a lot of ethical considerations surrounding blockchain itself. It is a technology that facilitates certain types of activities and products. Some have raised ethical concerns about these specific products. Most notably, there are questions about the moral considerations of cryptocurrencies in undermining existing national currencies. If this were to accelerate in meaningful ways, it could have catastrophic impacts on the global economy, with the greatest consequences for those populations not currently holding any bitcoin, which are most likely to be those who are already poor. There are also questions about the implications of replacing societal functions with blockchain processes. For instance, smart contracts (see Section 14.4.4) are a technology-driven alternative to existing legal processes in commerce. Though this might seem innocuous on its own, one must keep in mind that contracts are governed by existing legal regulations. The regulation of a smart contract is dependent on the computer code embedded in the design of the blockchain. This code governs the contract in ways that may or may not be consistent with established law. Also, because these aspects of the contract are embedded in code, it may be difficult for the average user to investigate whether all of the features of the contract are as expected. This is similar to concerns about the “user agreements” to which most people blindly consent when using a new web site.
14.4.4 Major Applications
Cryptocurrency is the most prominent application of blockchain but far from the only one. As noted in the previous section (Section 14.4.3), smart contracts are another popular use of blockchain for managing the stages of signature and ownership. The latter is especially important for the transfer of digital property, like “non-fungible tokens” (NFTs). NFTs enable people to own digital media, like viral YouTube videos, in the same way that they might want to own a painting or sculpture. In fact, art dealers and collectors are often faced with the difficulty of ensuring the chain of ownership of an item when trying to guarantee its authenticity. Blockchain offers a solution not only for the ownership of digital media but also for this long-standing challenge for non-digital media.
The specialized security of blockchain has inspired some to consider how it might be applied to voting. Though this concept is still in its infancy, it appears to be promising. If every individual or voting machine were its own node in the system, then once a vote is tallied it cannot be altered. This would protect elections from being compromised by hacking.
A final application capitalizes primarily on the data structure of blockchain to track the history of objects in a longitudinal database while maintaining information about their status at all points along the way. This has proven extremely valuable for tracking food through the supply chain. In this case a blockchain tracks the location of a batch of food from source to final delivery. If, for instance, there is an E. coli outbreak, authorities can quickly identify the source and any other potential points of contamination, as well as other batches that passed through the same locations and might be contaminated, too. A similar logic has been applied to tracking diamonds to ensure their ethical sourcing and to immunity in COVID-19 patients owing to their vaccination or previous infection.
14.5 Summary
In this chapter we have learned about three advanced analytic techniques that are increasingly used in urban informatics. We have learned how they work, when to use them, as well as ethical considerations and major applications. These include:
- Sensor networks that track environmental conditions across a city;
- 5G, the newest generation of the cellular network;
- Blockchain, which is an innovative way to create security in tracking the history of items.
The goal here was not to make you an expert just yet, but to expose you to the basic knowledge needed to meaningfully discuss these tools and their applications, as well as enable you to go out and learn more about them.
14.6 Exercises
14.6.1 Problem Set
- For each of the following pairs of analytic techniques and emergent technologies, describe how the first might be applied to or enabled by the latter (you may need to revisit previous chapters, especially Chapter 13).
- Network science and sensor networks
- Predictive analytics and sensor networks
- Artificial intelligence and 5G networks
- Inferential statistics and blockchain
- For each of the three technologies learned in this chapter, summarize what you think is the most important ethical concern.
- For each of the three technologies learned in this chapter, find and describe one additional application.
14.6.2 Exploratory Data Assignment
Research a particular application of one of the three analytic techniques presented in this chapter (or that combines two or more of them). Write a short memo that describes:
- The purpose of the policy, program, service, or product.
- How it uses the technique (or techniques) in question.
- How it does or does not address potential ethical considerations.
- How well the technique has been applied to this situation.